Back up and restore Nerdio Manager configuration
This article discusses how to back up and restore the Nerdio Manager configuration.
Post–February 2025: Updated backup strategy
As of February 2025, we updated our backup and restore strategy. The following sections outline our current recommendations on this topic.
Important: We encourage you to review and follow the updated processes. However, if you've already implemented the legacy backup method, you can continue using it as described in Pre–February 2025: Legacy backup strategy.
Nerdio Manager is an Azure application consisting of several PaaS services. When backing it up, consider the following components:
-
Azure Key Vault: This contains service principal secrets and AD domain joiner user account passwords. The contents of the Key Vault are fairly static and do not need to be backed up on a regular basis.
-
Azure SQL Database: This contains auto-scale configuration (for example, scheduling), logs, and auto-scale history data. The relevant contents of the database change when auto-scale settings are modified. A recurring backup is recommended.
-
Azure App Service: This runs the Nerdio Manager application and does not contain actual data beyond the application binaries. The contents of the app service change when the application is upgraded to the latest version.
Tip: The recommended method for backing up Nerdio Manager is to use the default backups for both the App Service and SQL Server, which are automatically configured by Azure when the resources are created. The process for configuring custom backups is covered below.
Since Azure does not provide a built-in backup process for Key Vaults, a script will be used to back up certificates, keys, and secrets.
For Nerdio Manager configuration components and their built-in restore functionality, see Nerdio Manager SQL Database Restore: Host Pool Matrix.
Prerequisites
Ensure the following prerequisites are met.
|
Area |
Details |
|---|---|
|
Scripts download |
Select this link to download the .zip file that contains the scripts used in the steps below. Once you download the zip file, unzip it on your local computer. |
|
Azure |
A non-guest account with at least Contributor role permissions on the Key Vault, which can be inherited from the subscription the Key Vault is tied to. |
|
Local system |
|
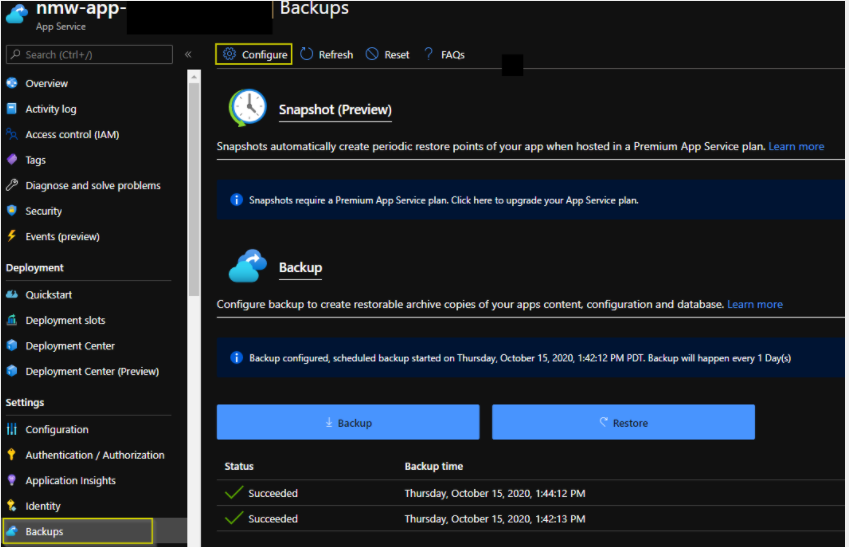
App Service automatic backups
By default, Azure enables an hourly automatic backup of the App Service.
To view the automatic backups:
-
In the Azure portal, navigate to App Services > NME App Service.
-
In the left menu, navigate to Settings > Backups.
The hourly automatic backups are displayed on this page.
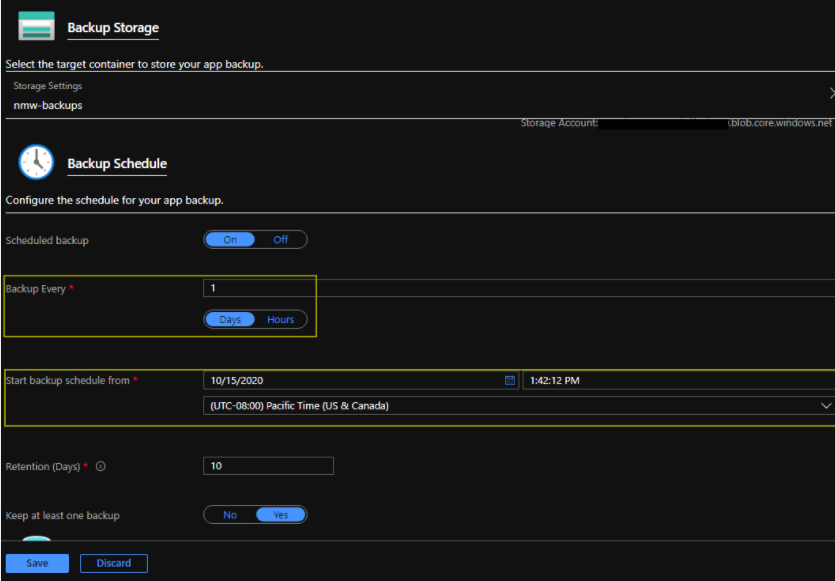
App Service custom backups
If needed, you can customize Azure automatic backups to use a specific schedule, custom retention settings, and include a linked database.
Note: Databases up to 4 GB can be backed up via the App Service backup. For larger databases, SQL Server-provided backups must be used instead.
For details, see Back up and restore your app in Azure App Service.
To back up the App Service and SQL database:
-
Locate the downloaded app-service-backup.ps1 script on your local computer.
-
Retrieve the following values:
Value
Steps
Azure subscription ID
Go to Nerdio Manager > Settings > Azure environment > Azure subscriptions tile.
Note: Both the App Service and backup storage account should be located in the same Azure subscription.
App Service resource group name
Go to Nerdio Manager > Settings > Azure environment > Linked resource groups tile.
App Service name
Go to Azure portal > Resource groups, and look up the name.
Storage account resource group
Go to Azure portal > Resource groups, and look up the name.
Note: This can be the same as the App Service resource group name.
Storage account name
Go to Azure portal > Storage accounts, and locate the name.
-
On your local computer, run the app-service-backup.ps1 script and provide the values as requested.
Note: When prompted to sign in, use an account with permissions to the App Service and storage account. A user with Contributor permissions on the subscription is recommended.
After the script runs, backups of the App Service and SQL database are performed automatically every day, with a retention period of 15 days.
Note: By default, the script sets a retention period of 15 days and runs every day at the same time it was initially executed.
To modify the retention period:
-
In the Azure portal, navigate to App Service.
-
Go to Settings > Backups, and select Configure custom backups.
-
Customize the settings as needed.
-
Ensure the SQL connection string is present before you select Save. If the value is missing, you can retrieve it from the Secrets tab in the Key Vault provisioned by Nerdio, under the name ‘ConnectionStrings—DefaultConnection’.
Alternatively, you can run the app-service-backup.ps1 script with the -retentionPeriodInDays parameter, specifying the desired retention period.
SQL Server backup
By default, Azure enables a daily automatic backup of the database. For detailed steps, see Change automated backup settings for Azure SQL Database.
To view and modify SQL backups:
-
In the Azure portal, navigate to SQL servers > NME SQL server.
-
In the left menu, navigate to Data management > Backups > Retention policies.
-
Modify the retention policy to change the backup frequency and retention periods.
Key Vault backup
You can back up the Key Vault using two alternative methods:
-
With the Backup NMW App scripted action in Nerdio Manager.
-
With a PowerShell script that retrieves the certificates, keys, and secrets stored within the Key Vault, and saves them to a local zip file named keyvault-backup.zip in the same directory where the script is run. The contents of the zip file are encrypted and can only be decrypted in the original Key Vault region in Azure.
Warning: This process creates a one-time backup. No scheduling is configured. If a recurring backup is required, you can schedule the Backup NMW App scripted action from Nerdio Manager.
To back up the Key Vault using a PowerShell script:
-
Locate the downloaded key-vault-backup.ps1 script on your local computer.
-
Retrieve the following values:
-
Azure Subscription name: Go to Nerdio Manager > Settings > Azure environment > Azure subscriptions tile.
-
Key Vault name: Go to the Azure portal and look up the name.
-
-
On your local computer, run the key-vault-backup.ps1 script and provide the values as requested.
Note: When prompted to sign in, use a non-guest account with Access policies and permissions for the Key Vault. A user with Owner role is recommended.
-
After the script runs, the keyvault-backup.zip backup file is present in the directory.
Note: Be sure to save the backup file (keyvault-backup.zip) in case you need it for a future restore.
Key Vault restore
The following procedure restores the Key Vault from a backup.
Note: The backups taken in the previous process only support in-region restores, meaning the restore process fails if the vault's contents are restored to a new region.
To restore the Key Vault from a backup:
-
Locate the downloaded key-vault-restore.ps1 script on your local computer.
-
Move the key-vault-restore.ps1 script to the same directory as the keyvault-backup.zip file.
-
Run the key-vault-restore.ps1 script.
Note: The script restores only keys, secrets, and certificates that do not exist. If they have been deleted, but not purged, you receive a conflict error from the script. When restoring to a Key Vault with existing values, those values are not overwritten.
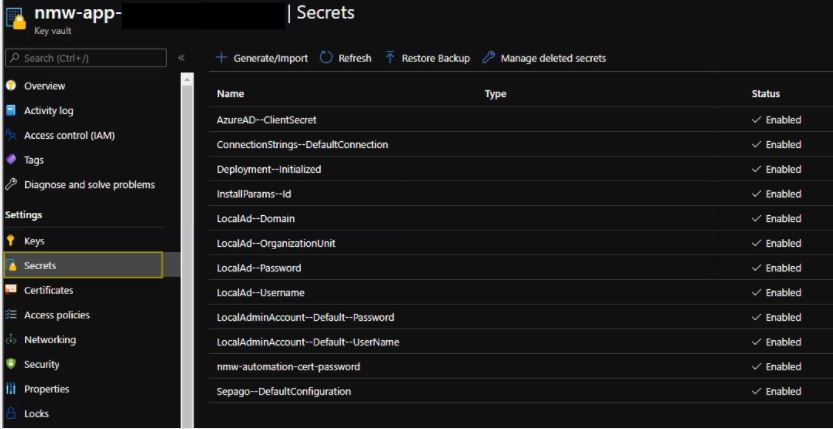
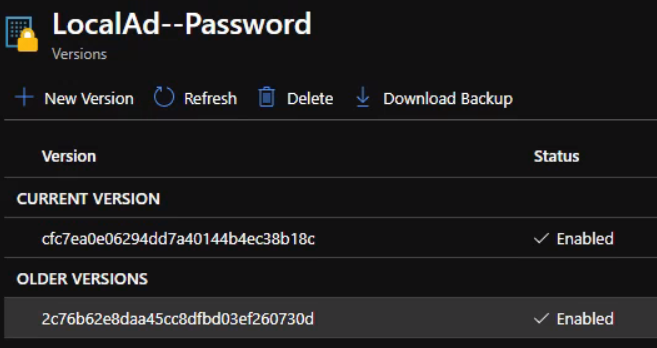
Note: You can manually restore old secrets from the portal by selecting the Older Versions of the secret. This is useful if a specific value has been changed and needs to be reverted, such as the password used by the AD account.
Pre–February 2025: Legacy backup strategy
This section covers how to back up and restore the Nerdio Manager configuration using the recommended backup strategy prior to February 2025.
Important: We encourage you to review and follow the updated processes as described in Post–February 2025: Updated backup strategy. However, you can still use the legacy backup method if already implemented.
Nerdio Manager is an Azure application consisting of several PaaS services. When backing up Nerdio Manager, consider the following components:
-
Azure Key Vault: This contains service principal secrets and AD domain joiner user account passwords. The contents of the Key Vault are fairly static and do not need to be backed up on a regular basis.
-
Azure SQL Database: This contains auto-scale configuration (for example, scheduling), logs, and auto-scale history data. The relevant contents of the database change when auto-scale settings are modified. A recurring backup is recommended.
-
Azure App Service: This runs the Nerdio Manager application and does not contain actual data beyond the application binaries. The contents of the app service change when the application is upgraded to the latest version.
Tip: The recommended method for backing up Nerdio Manager is to enable App Service backups and directly retrieve the contents of the Key Vault used by Nerdio Manager to a .zip file. SQL database backups are automatically included with the App Service backups.
For Nerdio Manager configuration components and their built-in restore functionality, see Nerdio Manager SQL Database Restore: Host Pool Matrix.
In this section:
|
Area |
Details |
|---|---|
|
Scripts download |
Select this link to download the .zip file that contains the scripts used in the steps below. Once you download the zip file, unzip it on your local computer. |
|
Azure |
|
|
Local system |
|
The following procedure backs up the App Service and SQL database.
To back up the App Service and SQL database:
-
Locate the downloaded app-service-backup.ps1 script on your local computer.
-
Retrieve the following values:
Value
Steps
Azure subscription ID
Go to Nerdio Manager > Settings > Azure environment > Azure subscriptions tile.
Note: Both the App Service and backup storage account should be located in the same Azure subscription.
App Service resource group name
Go to Nerdio Manager > Settings > Azure environment > Linked resource groups tile.
App Service name
Go to Azure portal > Resource groups, and look up the name.
Storage account resource group
Go to Azure portal > Resource groups, and look up the name.
Note: This can be the same as the App Service resource group name.
Storage account name
Go to Azure portal > Resource groups, and locate the name.
-
On your local computer, run the app-service-backup.ps1 script and provide the values as requested.
Note: When prompted to sign in, provide an account with permissions to the App Service and storage account. A user with Contributor permissions on the subscription is recommended.
-
After the script runs, backups of the App Service and SQL database are performed automatically every day, with a retention period of 15 days.
Note: By default, the script sets a retention period of 10 days and runs every day at the same time it was initially executed.
To modify the retention period:
-
In the Azure portal, navigate to App Service.
-
Go to Settings > Backups, and select Configure custom backups.
-
Customize the settings as needed.
-
Ensure the SQL connection string is present before you select Save. If the value is missing, you can retrieve it from the Secrets tab in the Key Vault provisioned by Nerdio, under the name ‘ConnectionStrings—DefaultConnection’.
-
You can back up the Key Vault using a PowerShell script that retrieves the secrets and certificates stored in the Key Vault, and saves them to a local zip file named keyvault-backup.zip in the same directory where the script is run. The contents of the zip file are encrypted and can only be decrypted in the original Key Vault region in Azure.
Warning: This process creates a one-time backup. No scheduling is configured. If a recurring backup is required, you can schedule the Backup NMW App scripted action from Nerdio Manager.
To back up the Key Vault:
-
Locate the downloaded key-vault-backup.ps1 script on your local computer.
-
Retrieve the following values:
-
Azure subscription name: Go to Nerdio Manager > Settings > Azure environment > Azure subscriptions tile.
-
Key Vault name: Go to the Azure portal and look up the name.
-
-
On your local computer, run the key-vault-backup.ps1 script and provide the values as requested.
Note: When prompted to sign in, use a non-guest account with Access policies and permissions for the Key Vault. A user with Owner role is recommended.
-
After the script runs, the keyvault-backup.zip backup file is present in the directory.
Note: Be sure to save the backup file (keyvault-backup.zip) in case you need it for a future restore.
You can restore the App Service using the portal option within the App Service, or using the files stored in the storage account under the nmw-backup blob container.
For details, see:
The following procedure restores the Key Vault from a backup.
To restore the Key Vault from a backup:
-
Locate the downloaded key-vault-restore.ps1 script on your local computer.
-
Move the key-vault-restore.ps1 script to the same directory as the keyvault-backup.zip file.
-
Run the key-vault-restore.ps1 script.
Note: The script restores only secrets and certificates that do not exist. If they have been deleted, but not purged, you receive a conflict error from the script. When restoring to a Key Vault with existing values, those values are not overwritten.

Note: You can manually restore old secrets from the portal by selecting the Older Versions of the secret. This is useful if a specific value has been changed and needs to be reverted, such as the password used by the AD account.
